 Azure administrators need to have Global Administrator role to work with MFA, particularly to import and activate OATH tokens. Sometimes they want to delegate this task to service desk team, but to achieve this they need to delegate GA rights too. In this article, we would like to talk about a couple of solutions that would be usefull for administrators in managing MFA.
Azure administrators need to have Global Administrator role to work with MFA, particularly to import and activate OATH tokens. Sometimes they want to delegate this task to service desk team, but to achieve this they need to delegate GA rights too. In this article, we would like to talk about a couple of solutions that would be usefull for administrators in managing MFA.
Definitely CSV file with tokens can be uploaded only with Global Admin role and there are no ways around it.
So, Global Administrator uploads the CSV file and activates tokens for all users. Activating tokens at once for all users can be done using our bulk activation tool. After this has been done for all users, there are some workarounds to delegate the remaining tasks to other type of tenant administators.
Below are the methods by which the administrator can partially delegate the rights to enable / disable MFA for users.
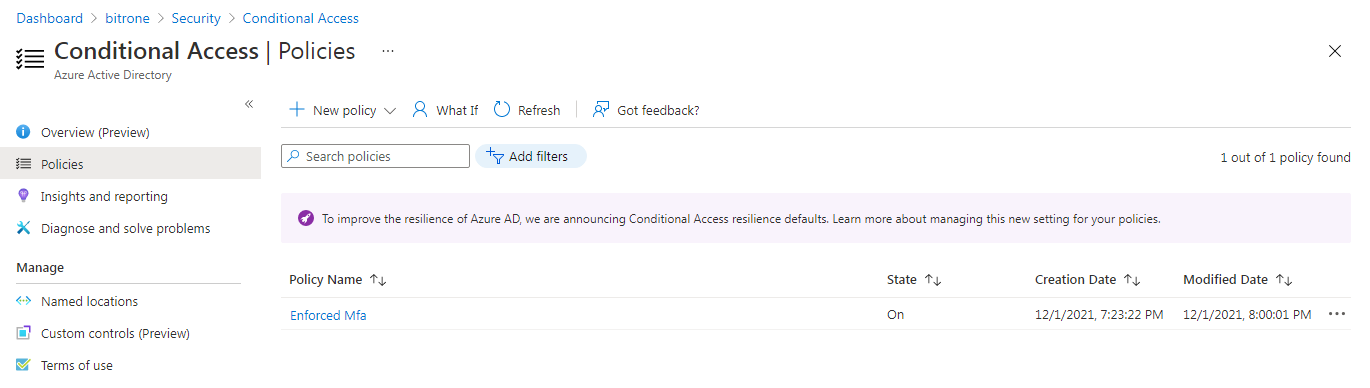
Method 1. Through Conditional Access
Administrator creates Conditional Access rule with MFA Enforced Group, delegates User Administrator role to service desk team.
This role is enough to be able to add a user to the group to activate MFA. If necessary, they can exclude user from this group and thus disable MFA for this user.
Method 2. Enable/Disable MFA for each user with Power Shell
Administrator delegates Authentication Administrator or Privileged Authentication Administrator roles to service desk team.
PS C:> Connect-MsolService
This cmdlet attempts to initiate a connection to Azure Active Directory.
PS C:> Get-MsolUser | fl UserPrincipalName, StrongAuthenticationRequirements
This cmdlet with pipeline shows status of MFA for all users:
StrongAuthenticationRequirements : {} - MFA is disabled
StrongAuthenticationRequirements : {Microsoft.Online.Administration .StrongAuthenticationRequirement}- MFA is enabled
To enable MFA :
PS C:> $mf= New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
PS C:> $mf.RelyingParty = "*"
PS C:> $mfa = @($mf)
PS C:> Set-MsolUser -UserPrincipalName [email protected] -StrongAuthenticationRequirements $mfa
To disable MFA :
PS C:> Get-MsolUser -UserPrincipalName [email protected] | Set-MsolUser -StrongAuthenticationRequirements @()
integration guides
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
