Hardware tokens for PPTP VPN on Windows Server using TOTPRadius

TOTPRadius can be used if you need to have hardware tokens as the second factor for two-factor authentication with Windows Server based PPTP VPN.
You can enroll the same tokens as with Azure MFA, so your users can use the same hardware token for both Office 365 and VPN Access.
PPTP server allows using external RADIUS servers as the authentication source and this will allow implementing two-factor authentication using Token2 TOTPRadius appliance as a more cost-effective alternative to the standard methods, as the same hardware tokens can be used for accessing multiple systems.
TOTPRadius is deployed as a software-based virtual appliance that runs on two hypervisors: VMWare ESXi and Microsoft Hyper-V. It is free to use with up to 5 users. You can download appliance from our site.
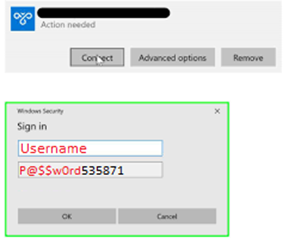
In this guide, we will show how to configure a PPTP VPN to work with TOTPRadius in LDAP proxy mode. The authentication will use the standard login forms (username+password only) and the password field is expected to have the LDAP password followed by 6 digit OTP as a single string. For simplicity, this guide will show configuring accounts with administrative access.
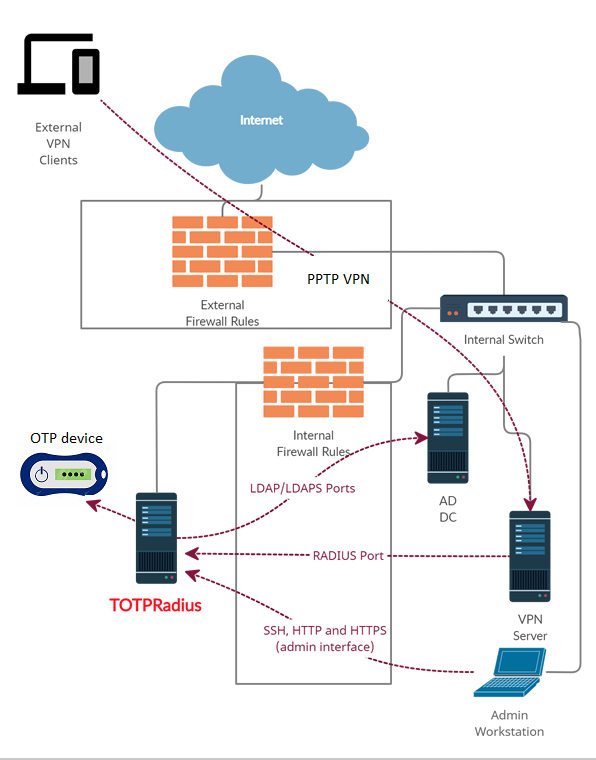
The principle behind LDAP proxy feature of TOTPRadus is that users will provide their AD or LDAP password together with the one-time passwords in the password field. TOTPRadius will then parse the password, split it into two parts and authenticate the OTP and if correct will send the AD/LDAP password part further to the AD/LDAP server configuration. This setup was tested only with Microsoft Active Directory as the LDAP backend.

![]()
The setup described in this guide is based on the following components:
· Active Directory deployed on Windows Server 2016 ( ip: 192.168.50.10)
· Token2 TOTPRadius v0.2.5 with built-in free 5 users license( ip: 192.168.50.234)
· Classic or a programmable Token2 TOTP hardware token used as the second factor
· Server 2016 with Routing and Remote Access role enabled- PPTP server ( ip: 192.168.50.237)
Step1. Configure TOTPRadius in LDAP Proxy mode
in LDAP settings section:
· Set LDAP server (hostname or IP for regular LDAP and ldaps://ip_or_hostname for LDAPS). Separate multiple servers with spaces
· Put your NETBIOS prefix or UPN suffix in the username format field keeping %username% string. I.e. if a user in your AD environment is using [email protected] to log in, the username format field should be set as "%username%@domain.com"
· You also need to define an LDAP search string to allow the LDAP connection session to locate the users' OU (i.e. 'ou=users,o=myorgname').
· If you need the user to self-enroll the second factor, enable "Allow LDAP Enrollment" option
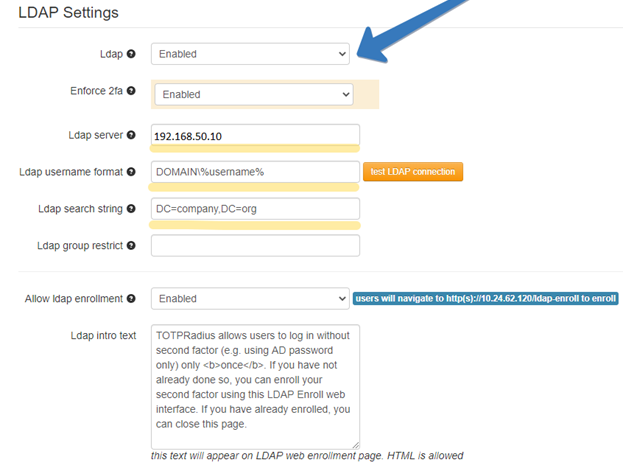
Also, we need to copy out radius secret for using in VPN server side.
![]()
Step2. Configure Radius server in Routing and Remote Access side (VPN Server).
Right button on VPN server name, click properties. Then click Configure:
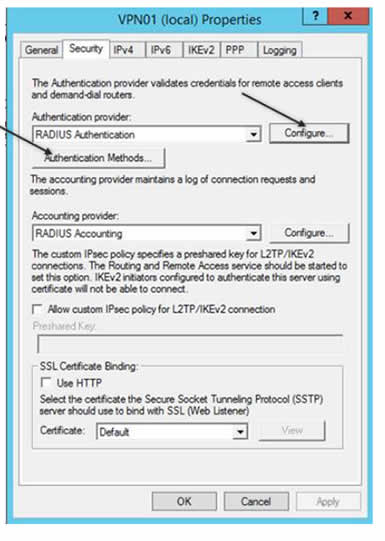
Then we must add Radius server. Specify TOTPRadius IP address and its secret key, which we previously copied from TOTPRadius :
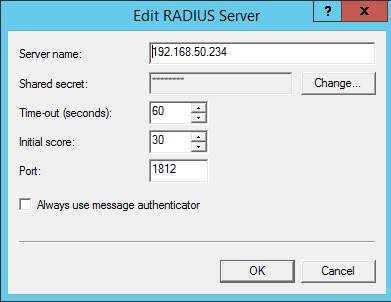
Then we click Authentication Methods button and leave only 1 option, PAP:
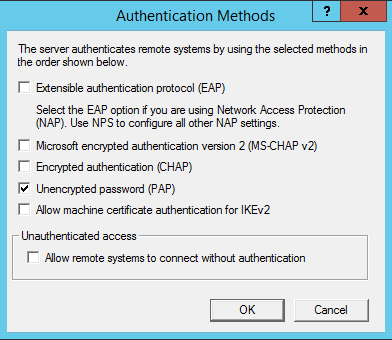
Step 3. Generate or set the second factor for the user on the TOTPRadius appliance.
Second factor for the user can be added in two ways:
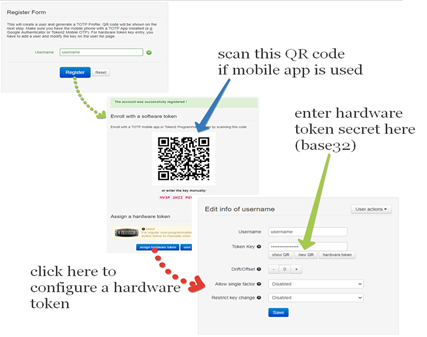
1) By self-enrollment. Users can enroll their hardware tokens themselves using link http://(totpradius server_ip)/ldap-enroll :
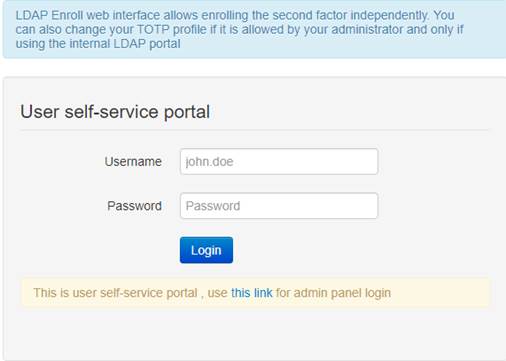
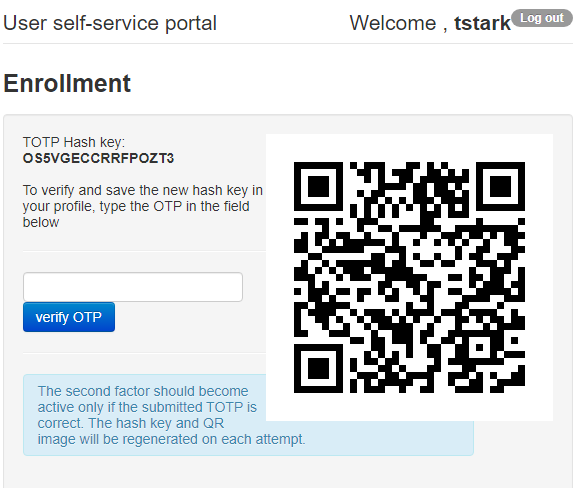
Self Enrollment is possible having used programmable hardware, you can burn the secret onto the hardware token by scanning the QR code using one of the NFC Burner apps.
2) By TOTPRadius admin. Login to TOTPRadius admin interface, and click on New User button. This will generate a QR code that should be used to provision the TOTP profile on a mobile authenticator app (Google Authenticator, Microsoft Authenticator, Token2 TOTP+ or any other RFC6238-compliant application). If a hardware token is to be used for this user, click on Edit profile or assign hardware token button and paste the secret key of the hardware token in Token key field in base32 format.
You should now be ready to log in
After all 3 steps above are completed successfully and without errors, the user can log in with VPN connection using his/her username and active directory password and the 6 digit OTP generated by the hardware token. Also, do not forget to specify unencrypted password(PAP) option in VPN connection settings.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
16-09-2025
Token2 PIN+ Keys Now Supported by MojeID at High Assurance Level
 MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
MojeID, the Czech national digital identity service operated by CZ.NIC, has officially added Token2 PIN+ security keys to its list of devices accepted for the high assurance (úroveň záruky vysoká) level.
18-07-2025
Windows 11 Update KB5062553 Breaks FIDO2 Security Key Management
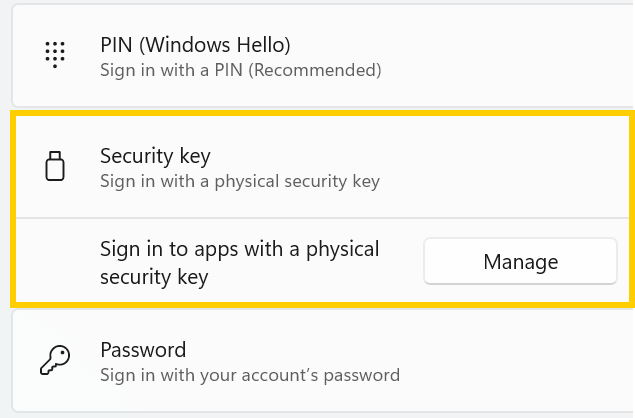 A recent Windows 11 update — KB5062553 — appears to have introduced a critical issue affecting FIDO2 security key management. Update as of 12 September 2025 – This issue is resolved in Windows 11 24H2 (build 26100.6584, KB5065426).
A recent Windows 11 update — KB5062553 — appears to have introduced a critical issue affecting FIDO2 security key management. Update as of 12 September 2025 – This issue is resolved in Windows 11 24H2 (build 26100.6584, KB5065426).
