How to Set Up 2-Factor Authentication in VMware Horizon View with TOTPRadius
VMware Horizon View enables you to access a virtual desktop from anywhere, anytime. Horizon offers you the possibility to move from one place to another: to work from your office or from a cybercafé, or from any other place, when you have a network connection that lets you connect to the Horizon View infrastructure.
This document describes how to secure your external connections and authorize only specific users or groups of users connecting to Horizon View from outside, using 2-Factor authentication with hardware tokens or mobile apps by integrating our TOTPRadius solution.
Prerequisites
Prerequisites are the following:
• vSphere Infrastructure correctly configured for Horizon View
• Horizon View correctly configured (Connection Server, Security Server and Composer)
• At least one TOTPRadius appliance deployed and configured
• Administrative access to both TOTPRadius and Horizon View
View Connection Server setup
Connect to your Horizon View Connection Server as Administrator

Select the Horizon View Connection Server you want to use: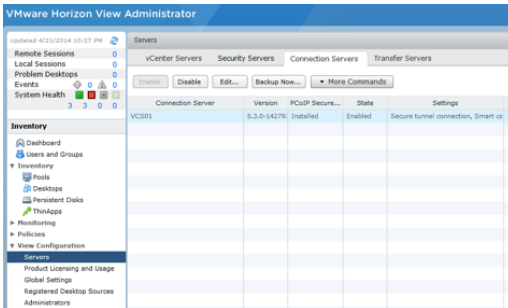
On Authentication tab, select RADIUS as “Advanced Authentication”: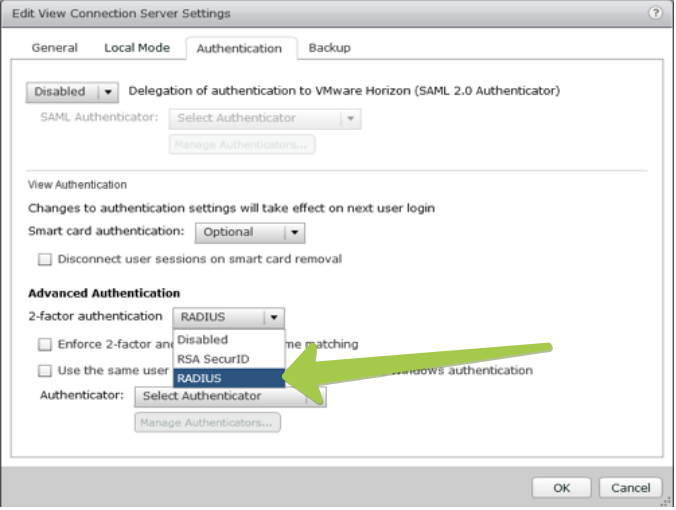
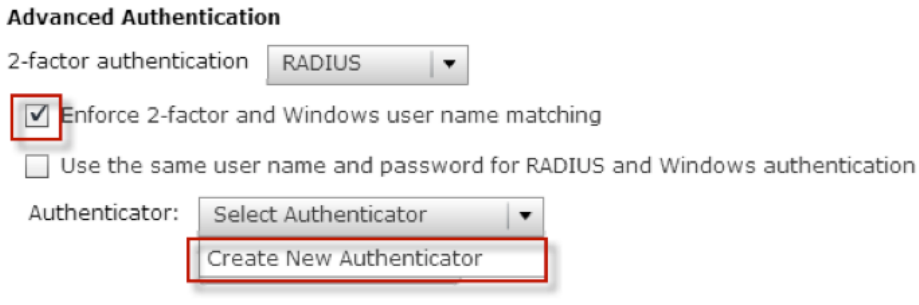
1. Check : “Enforce 2-Factor and Windows username matching”
2. Select: “Create New Authenticator”
3. Specify the Label : example : TOTPRadius
4. Specify the Hostname/Address : FQDN or IP address of your radius server
5. Specify the Shared Secret : the secret you specified in TOTPRadius settings
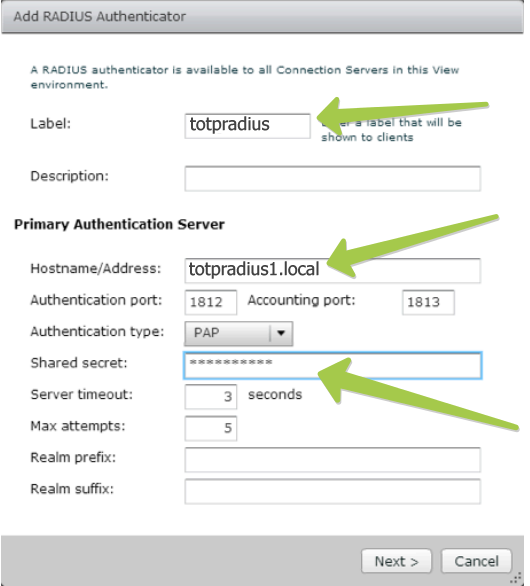
The shared secret should match the settings of your TOTPRadius appliance:
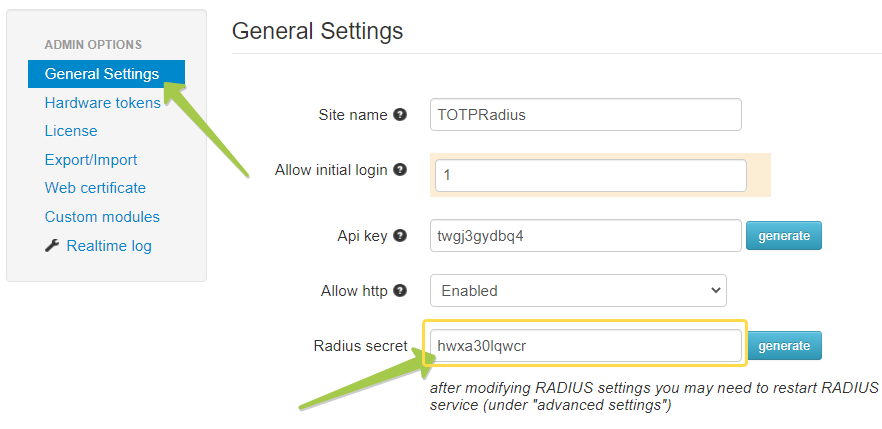
Note: For production usage, you can install and configure a secondary TOTPRadius server, in slave mode.
Adding users to RADIUS
At this point, Horizon View is configured 2-Factors authentication using your TOTPRadius server, now you have to add users to TOTPRadius. There are 2 methods: LDAP self-enrollment and creating users using Admin panel.
LDAP self-enrollment
Guide your users to navigate to https://FQDN_of_TOTPRadius//ldap-enroll and follow the instructions. The process will look like shown in the video below:
Creating users via Admin panel
Login to TOTPRadius admin interface, and click on New User button. This will generate a QR code that should be used to provision the TOTP profile on a mobile authenticator app (Google Authenticator, Microsoft Authenticator, Token2 TOTP+ or any other RFC6238-compliant application). If a hardware token is to be used for this user, click on Edit profile or assign hardware token button and paste the secret key of the hardware token in Token key field in base32 format.
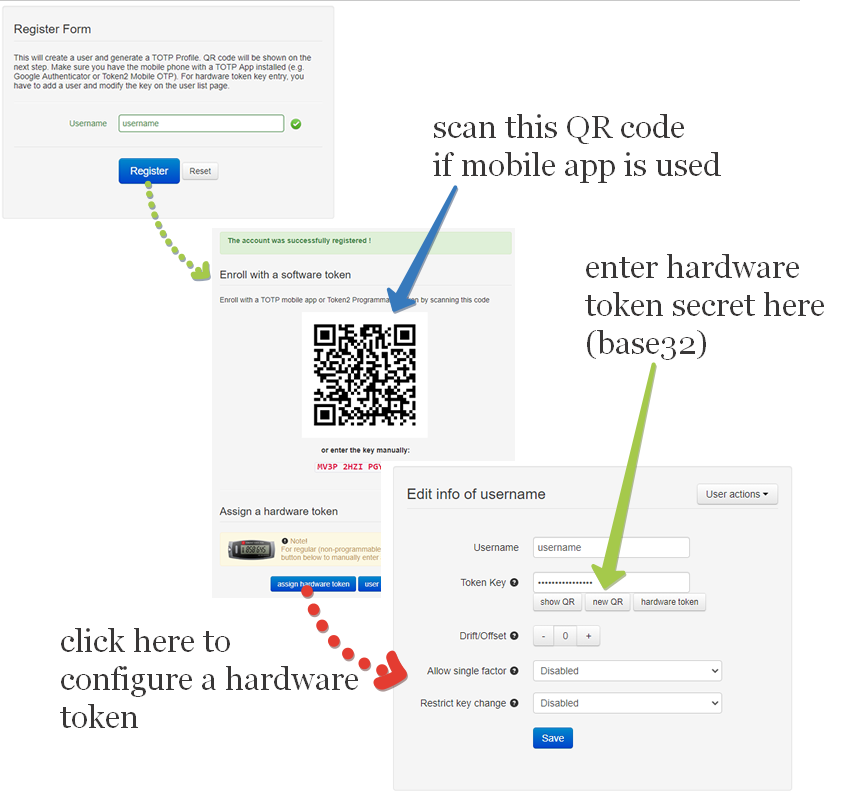
If a programmable hardware token is used, you can burn the secret onto the hardware token by scanning the QR code using one of the NFC Burner apps.
Logging in to Horizon View with 2FA enabled
Now you can test and make a connection on your View Connection Server by providing your login name and password in the form of "AD_PASSWORD""Generated Code" (no spaces nor quotes. I.e. if your password is MyP@ssword and the OTP code is 123456, you should enter MyP@ssword123456):
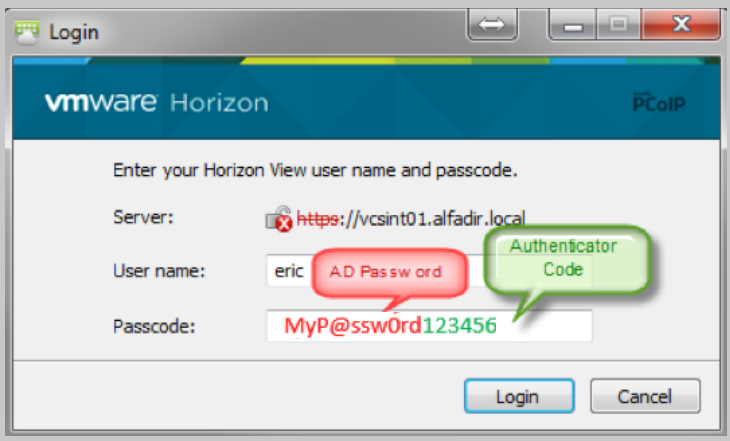
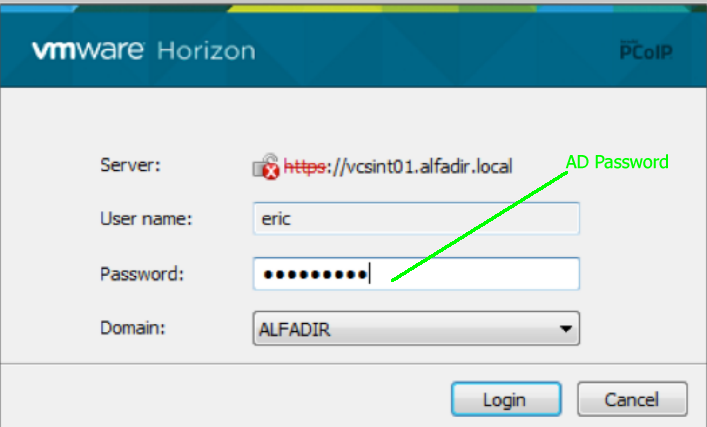
If everything works fine, the second login screen appears and you have to type your AD password only again (this is a hard-coded design by Horizon View whatever 2-Factor authentication method you want to use, and is not caused by TOTPRadius)
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
05-03-2026
Introducing TOTPVault — self-hosted TOTP management for teams
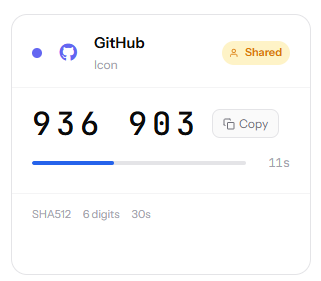 Most TOTP apps work by distributing copies of the secret to every person who needs access — fine for personal accounts, but for shared service accounts it means MFA secrets scattered across people's phones with no clean way to revoke access when someone leaves.
Most TOTP apps work by distributing copies of the secret to every person who needs access — fine for personal accounts, but for shared service accounts it means MFA secrets scattered across people's phones with no clean way to revoke access when someone leaves.
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
