Unlock Linux LUKS encrypted drives with Token2 FIDO2 Security keys
 LUKS (Linux Unified Key Setup) is a specification for block device encryption.It establishes an on-disk format for the data, as well as a passphrase/key management policy.
LUKS (Linux Unified Key Setup) is a specification for block device encryption.It establishes an on-disk format for the data, as well as a passphrase/key management policy.LUKS uses the kernel device mapper subsystem via the dm-crypt module. This arrangement provides a low-level mapping that handles encryption and decryption of the device’s data. User-level operations, such as creating and accessing encrypted devices, are accomplished through the use of the cryptsetup utility.
In this guide, we will show how to use Token2 security keys to unlock LUKS encrypted drives. We used Linux Fedora 39 in this guide , but it should work with slight modifications with any other Debian distributions(systemd>=250 is required).
Requirements:
• A Linux Fedora PC with a LUKS encrypted drive• Root access to run commands
• A Token2 FIDO security key with PIN set
Find your encrypted LUKS disks
We need to find the filesystem path(s) to the LUKS encrypted partition(s). Use lsblk to find them.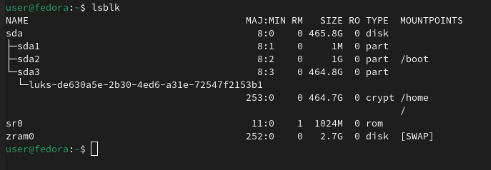
Find the partition number(s) hosting the luks- partition of type crypt. In this case, that’d be /dev/sda3. Use this path as the target for the following sections.
Enroll the Token2 security key
Start by verifying that systemd-cryptenroll can see and use your Token2 FIDO2 Security key: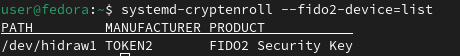
Now, enroll the security key , replacing /dev/sda3 with the block device of the LUKS encrypted drive.
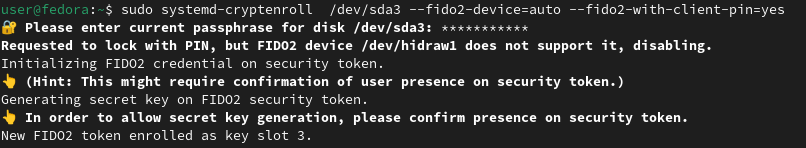
Every newly enrolled security key occupies a subsequent slot.
Modify /etc/crypttab
We need to modify /etc/crypttab in order to tell cryptsetup to unlock the device using the Token2 security key. Add fido2-device=auto in the options field of the crypttab entry for your device. For example: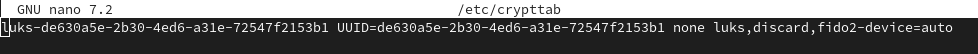
Finally, rebuild your initramfs using dracut. The following command will rebuild your currently-booted initramfs slot.

Note: with Fedora Silverblue, the final command should be rpm-ostree initramfs --enable --arg=f
You’ll now be prompted at boot to enter the PIN of your FIDO key. Be aware that the PIN entry prompt looks exactly the same as the passphrase prompt.
You will notice a difference only when using the terminal (which you can view by hitting the ESC key). After entering the correct PIN the hardware token will prompt you to touch it which (also) is not indicated on the prompt.
If it does not prompt for a touch, then systemd-cryptenroll was not able to find a hardware token corresponding to the entered PIN.Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
