Using Token2 FIDO2 Security keys for Authelia IAM
 Authelia is an open-source authentication and authorization server and portal that fulfills the identity and access management (IAM) role of information security
by providing multi-factor authentication and single sign-on (SSO) for your applications via a web portal. It acts as a companion for common reverse proxies like
nginx, Traefik, caddy or HAProxy to let them know whether requests should either be allowed or redirected to Authelia's portal for authentication.
Authelia is an open-source authentication and authorization server and portal that fulfills the identity and access management (IAM) role of information security
by providing multi-factor authentication and single sign-on (SSO) for your applications via a web portal. It acts as a companion for common reverse proxies like
nginx, Traefik, caddy or HAProxy to let them know whether requests should either be allowed or redirected to Authelia's portal for authentication.For this guide, we chose to use Nginx Proxy Manager as reverse proxy software. The Nginx proxy manager (NPM) is a reverse proxy management system running on Docker. NPM is based on an Nginx server and provides users with a clean, efficient, and beautiful web interface for easier management.
The guide assumes that you have already had a working instance of Authelia, and we will show the procedures required to configure the Webauthn 2FA method for it.
Authelia allows using Token2 security keys for two-step verification.
Requirements:
• A Server with Docker, Docker-Compose,Nginx Proxy Manager , and Authelia Installed and Ready• A FQDN address domain/ Sub-domain you want to use for the your Authelia portal (e.g. auth.example.com)
• An A-record pointing to the Public IP address where your server is.
• A Token2 FIDO security key
Enable an MFA method
The Settings for Authelia can be set using the files below:authelia/config/configuration.yml
authelia/config/users_database.yml
The Users Database file settings
Create a user database that contains the users who want to access your services. Run "nano users_database.yml" inside the config folder: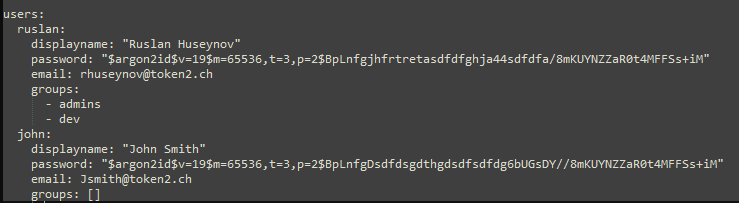
To create a hash password, use the command below:
docker run authelia/authelia:latest authelia hash-password 'yourpassword'
The Configuration file settings
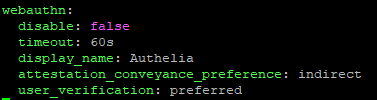
For activating the TOTP 2Fa method and assigning it, you need to have some values in the configuration.yml file. Run the "nano configuration.yml" command from the terminal and add the values below:1)Activate the Webauthn method.
2)We will deny access to everyone and turn on 2FA authentication for Authelia web portal (auth.example.com).
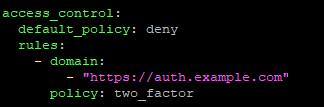
You also need to pay additional attention to the SMTP settings in this file. SMTP relay should work without any issues; otherwise, you will not be able to use 2FA methods.
Run "docker restart authelia" to restart the container with new settings.
Now go to the https://auth.example.com web portal. You should be prompted to login. You can now enter your username and password and make sure you're able to login.
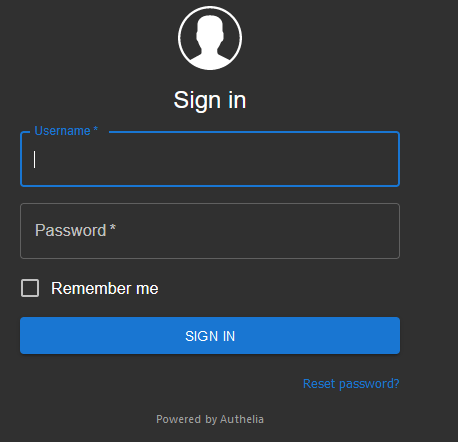
Click the "Register Device" button.
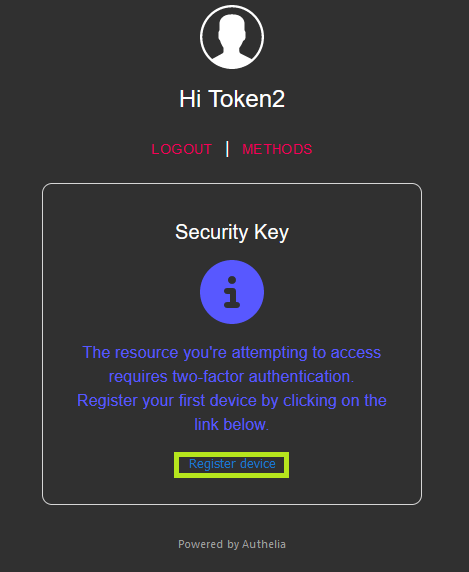
An email will be sent to your address to complete the process. Open your email from the same browser you were authorized to https://auth.example.com. Click on the "Register" button.
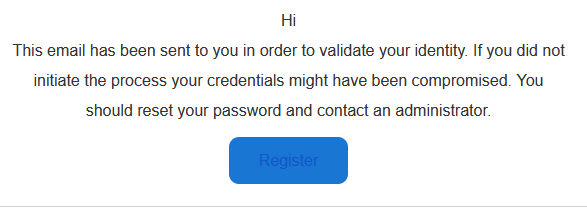
Authelia will start to identify the inserted security key.
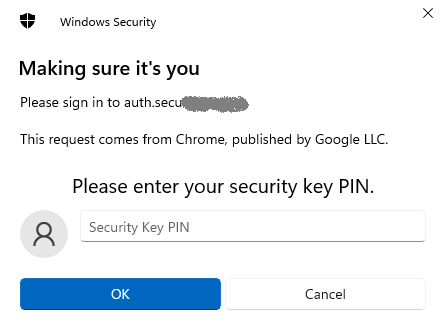
If you have set up a PIN code on it,you will be prompted to type it.
Then you will be prompted to press the button on the security key to complete registration. Note: Security keys differ in the exact instructions to activate them. Your key may require a tap or button press to activate registration.
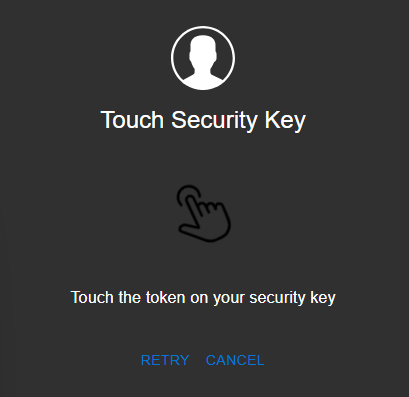
After the code is verified, you will be notified that you are authenticated.
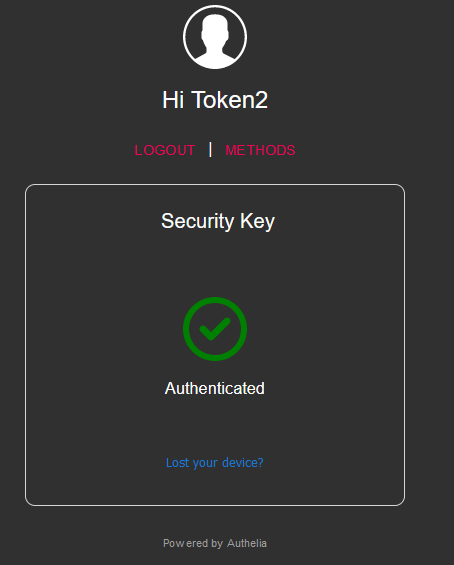
Then you will be redirected to your resources.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
